How To Recover Files That Are Deleted From Recycle Bin
How To Recover Files That Are Deleted From Recycle Bin
Well, Windows users have a bad habit of removing files from recycle bin. Deleting useless files from Recycle Bin helps a user to save some storage space which can improve the speed of a computer. However, Windows users do that more frequently and later regret. Actually, Recycle Bin is a place from where we can get back our deleted files and folders.
Sometimes, we accidentally delete our important files and folders and due to some reason we lose them from Recycle bin too! At that time, we search for recovery methods. Well, there are many methods available over the web which can help you to recover deleted files from computer, but, when it comes to reliability, nothing can beat EaseUS.
What Is EaseUS Data Recovery Wizard?
EaseUS is one of the leading software providers which is known for its data recovery programme. EaseUS offers some free data recovery software that can help you to recover deleted, formatted or lost data from PC, laptop or removable device easily and quickly.
One of the best thing about EaseUS is that it provides tools for recycle bin recovery which can help you to get back files that you have deleted from the Recycle bin itself. EaseUS Data Recovery Wizard free can easily recover lost files, pictures, documents, videos and more from deleting, formatting, partition loss, OS crash, virus attack and other data loss cases.
How To Recover Deleted Files?
If you are struggling to get back your lost data files, then here is an easy data recovery method which will help you to get back deleted files on your computer. Below, we are going to share a mini guide on how to use EaseUS Recycle Bin Recovery to get back your deleted data.
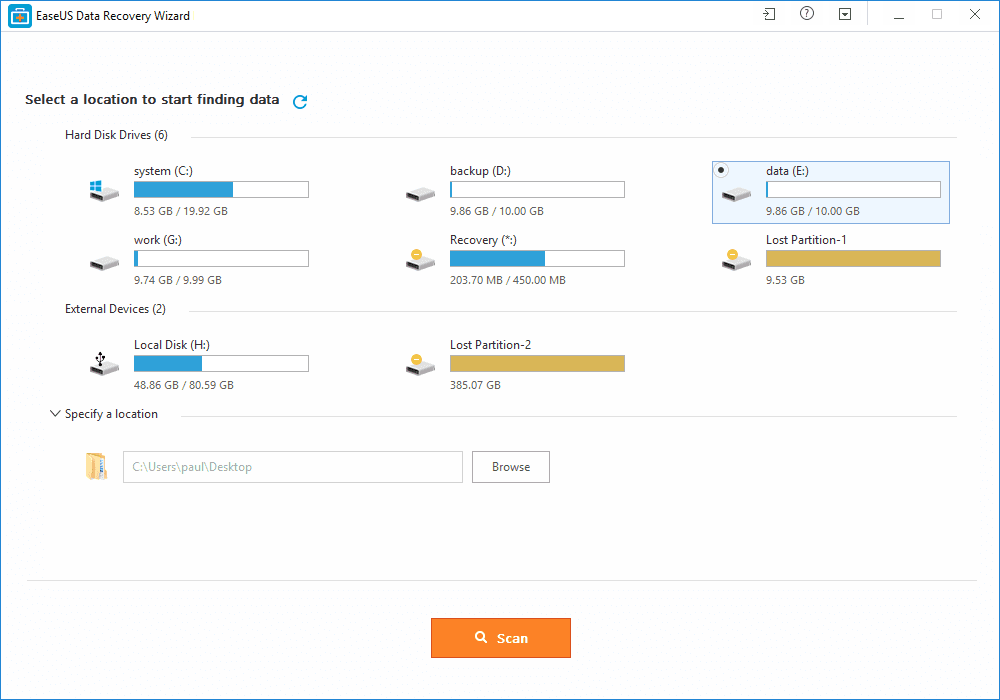
Step 1. First of all, you need to download and install EaseUS Data Recovery Wizard on your Windows computer and then launch it normally. You need to select the location where you want to scan and then click on 'Scan'
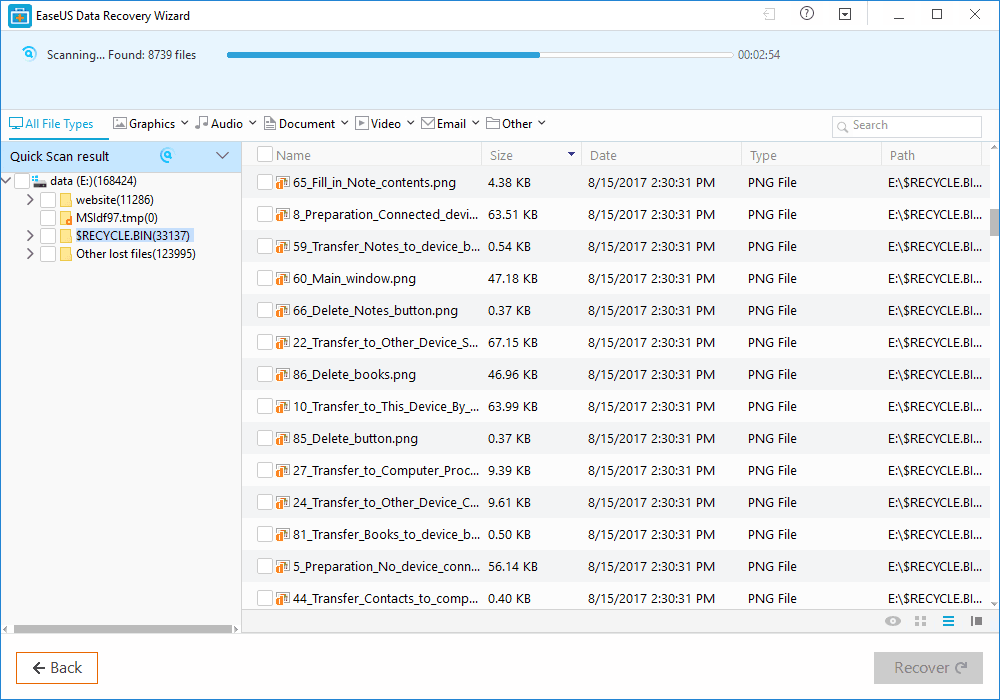
Step 2. Now, wait for few minutes until the tool finishes scanning your drive. The tool search for files that got deleted or cleaned from the Recycle Bin.
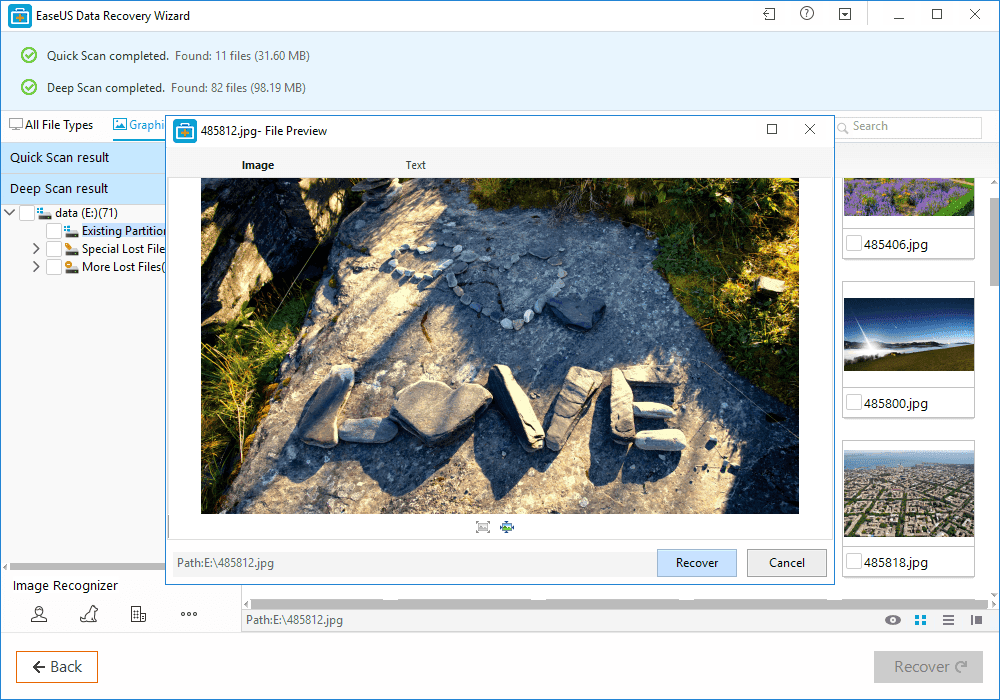
Step 3. Now it will show you files that you can recover. Here you need to click on the file which you want to recover and click on 'Recover'
That's it, you are done! This is how you can use EaseUS data recovery to get back your deleted files on your computer.
Benefits of EaseUS Data Recovery
Well, the data recovery tool provided by EaseUS comes with many benefits. It can not only recover accidentally deleted files, but it can also recover data in case of Virus Attacks, Hard Disk Damage, OS Crash etc.
You can also use this awesome data recovery wizard to recover deleted files from External Disk, USB Drive, Camcorder, Mobile Devices, Zip Drive, iPod, Music Player and more.
Overall, this is one of the best data recovery tools you can have on your Windows computer. EaseUS Data Recovery also has a free version with restricted features. Overall, this is a stress-free solution to get back your deleted files
More articles
- Pentest Tools Github
- Hacking Tools And Software
- Best Hacking Tools 2019
- How To Install Pentest Tools In Ubuntu
- Hack Apps
- Hack Tools Pc
- Hacker Tools Software
- Pentest Tools List
- Hack Tools Download
- Hacker Search Tools
- New Hacker Tools
- Hacking Tools Windows 10
- Hacker Tool Kit
- Tools Used For Hacking
- Hacking Tools For Mac
- Pentest Tools Framework
- Hacker Tools For Mac
- Hacker
- Tools 4 Hack
- Hacking Tools Software
- Hacker Tools Free Download
- Pentest Tools Github
- Hacking Tools For Kali Linux
- Pentest Tools Kali Linux
- Pentest Tools For Ubuntu
- Hacker Tools 2019
- Underground Hacker Sites
- Termux Hacking Tools 2019
- Hacks And Tools
- Hacker Tools
- Hacker Tools List
- Hacker Tools Github
- Hacking App
- Pentest Tools Apk
- Hack Tool Apk
- Best Hacking Tools 2019
- Best Hacking Tools 2020
- Hacker Tools Windows
- Pentest Tools Nmap
- Hack And Tools
- Hackrf Tools
- Hacking Tools Hardware
- Hacking Apps
- Hacker Tools For Ios
- Pentest Tools Linux
- Ethical Hacker Tools
- Hacker Tools Free Download
- Hacker Tools 2019
- Tools Used For Hacking
- Hacking Tools Hardware
- Hacker Tools Mac
- Best Hacking Tools 2020
- Hacking Tools Windows
- Hack Tools Pc
- Hacking Tools For Windows 7
- Usb Pentest Tools
- Pentest Automation Tools
- Pentest Tools For Ubuntu